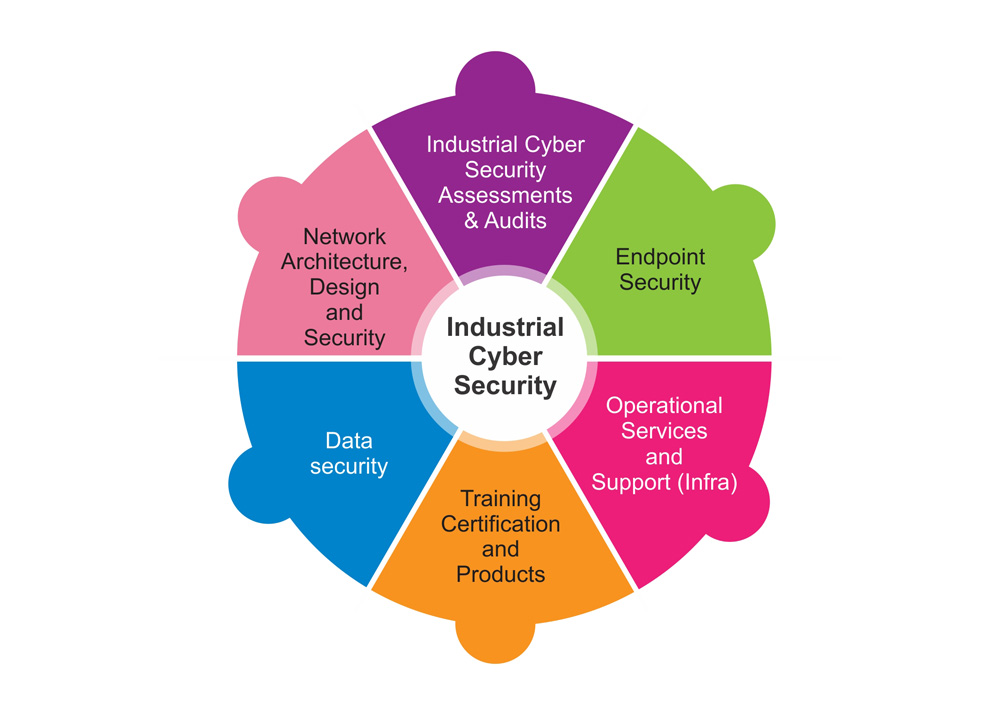
Industrial Cyber Security Management:
NONC is the leading Industrial Cyber Security company which provides services and solutions to secure and protect the critical infrastructure and operations of industrial automation and Control systems (IACS) in Oil and Gas, Power, Metals, Mining and Minerals, Water, paper and pulp, chemical, pharmaceutical, food and beverage, as well as discrete manufacturing (e.g. automotive, aerospace, and durable goods) companies as well as RAIL/Metro, IT and Telecom sectors.
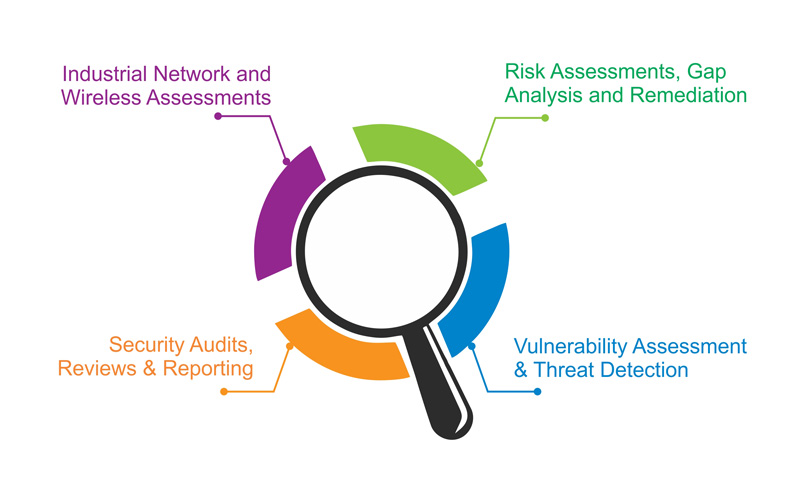
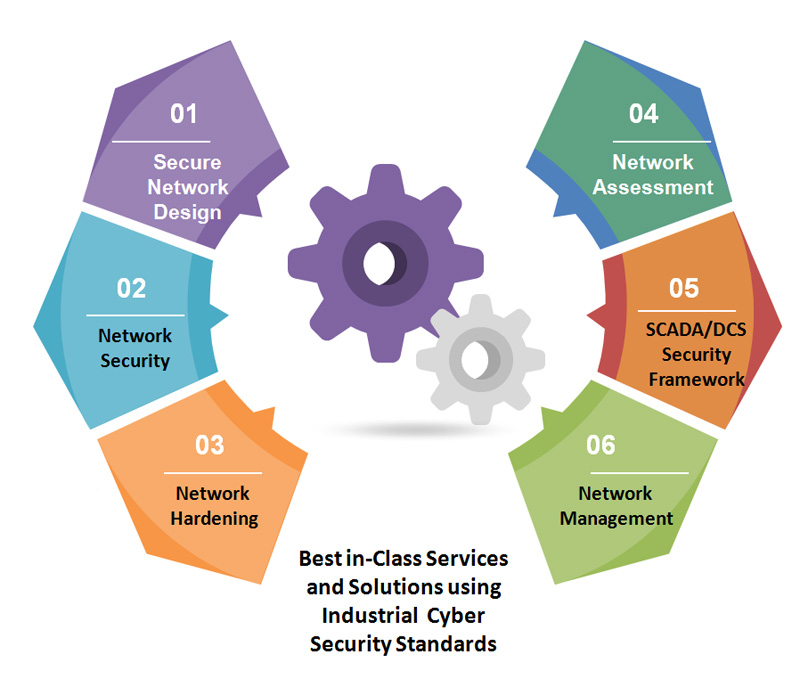
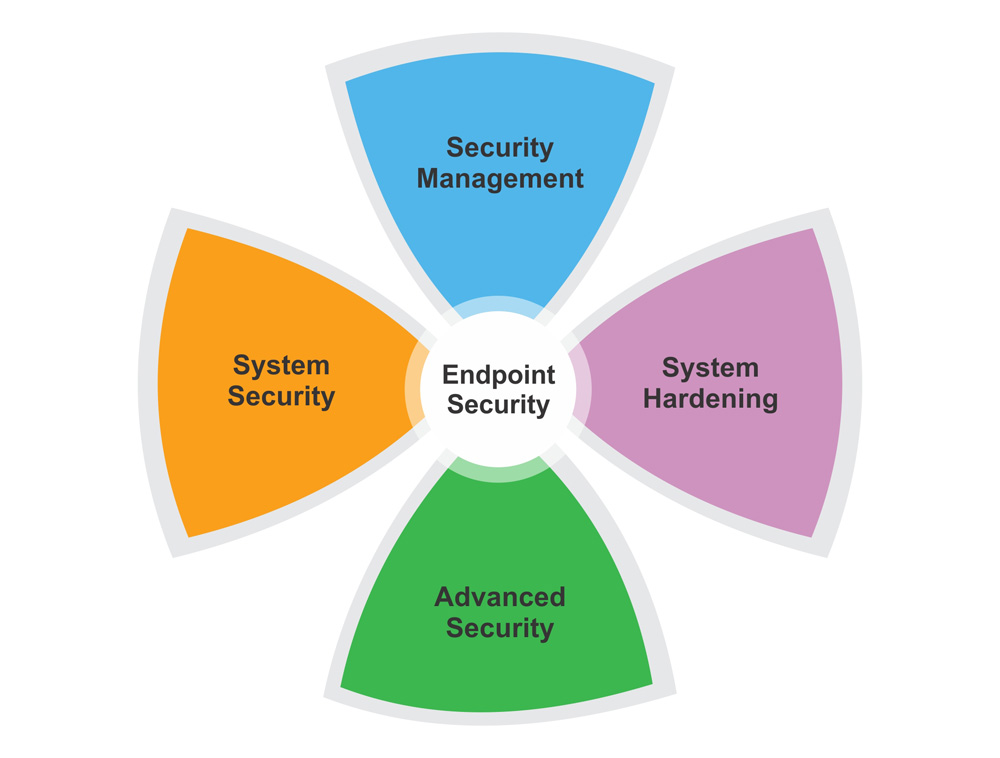
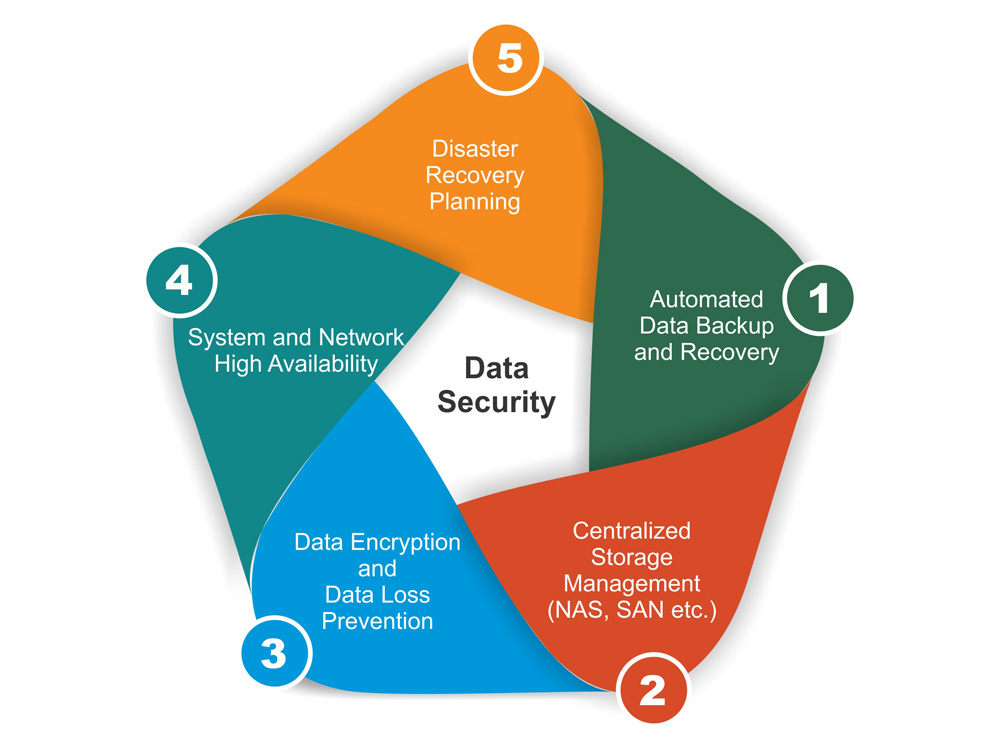
NONC can provide:
Industrial control systems (ICS) form the backbone of national critical infrastructure such as Electricity, Water and water treatment, Oil and gas etc. Hence the availability of ICS is critical to assuring safety, security and profitability. Historically, ICS components were not connected to IT networks or systems. But modern ICS are digitally interconnected and converges with business networks for significant efficiency gains due to adoption of new control technologies such as IIOT. This creates greater risk due to external threats to ICS and increases the possibility of cyber security vulnerabilities and incidents.
We make sure that Greenfield and Brownfield implementations of ICS are properly secured by various security measures to protect the industrial automation and control systems from external threats as well as the local ones.